A Step-by-Step Guide to Understanding a Network Takeover
How do cybercriminals break into an organization? It can be startlingly quick and easy. We’re going to take you through the step-by-step process of how hackers get into your computer and environment with very little time and resources, then expand their access to take over your entire network and even deploy ransomware. Along the way, we’ll also share prevention strategies to minimize the damage.
The Most Common Initial Access Attack Targets
CISA has identified the top five ways attackers gain initial access to a network as:
- Exploiting a public-facing application
- External remote services
- Phishing
- Trusted relationship
- Valid accounts
One of the most popular initial access attacks is phishing. The 2022 Verizon Data Breach Investigation Report found that 82% of breaches involved a human element – e.g. social engineering – and over 60% of those attacks were a result of phishing. Hackers can create a simple malware program that opens up a backdoor to your network in as little as 30 minutes. Then it’s a simple matter of creating a phishing email.
However, today’s criminals don’t even need to put in that much effort. It’s easy and inexpensive to buy a phishing and malware as-a-service kit that comes with everything from the phishing email to the fake payment screens that steal your information. As you can see in the screenshot from a dark web marketplace below, hackers can buy an inexpensive kit – including several choices of spoofed page templates for major brands – to quickly start a malware campaign.
How Hackers Get into Your Computer & Environment
To give you a real-world look at how hackers get into your computer and environment, we created a fake company, HackMe, Inc., with a victim employee named Erik L. User. Then, we recreated a common network environment with standard accessories and security and “seeded” HackMe with file repositories that included emails, invoices, Personally Identifiable Information (PII), and more. Now we’re ready to set our hacker loose and see what he can find.
Our hacker in this simulation is our Penetration Testing Team Manager, Tom Pohl. In this scenario, we’ll call him “Evil Tom.” We’ll walk you through each step Evil Tom takes to attack and breach HackMe’s environment and share how you could block that attack or minimize the damage. Read to the end and we’ll provide a link to a video recording of this HackMe takeover!
1) Initial Entry – The Phishing Attack! One of the top ways hackers break into your environment is by tricking an employee into clicking on a link or attachment in a phishing email. In this incident, the hacker sends our victim a fake Amazon invoice that contains a link to an executable program. 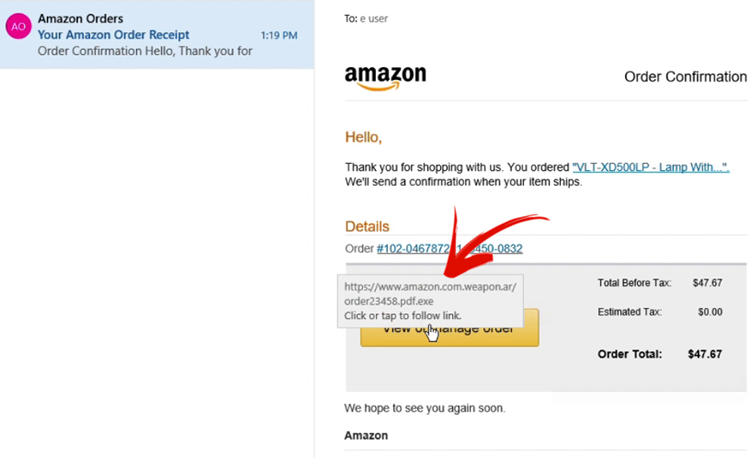
Once Erik clicks on the link, it looks like he links to a standard, legitimate Amazon screen. So, he enters his username and password and sees his account information, but he does not see the invoice in question. What’s actually happening? When Erik clicked the link, the executable program Evil Tom wrote ran several Windows utilities and initiated a connection to Evil Tom’s remote server. Then, the malicious script opened a persistent backdoor into Erik’s computer. Nine seconds after Erik clicked the link, Evil Tom attained persistent access to the HackMe network.
How can you prevent this from happening?
- Prevent spam and phishing emails from getting through to your users. You can do this using Microsoft 365 anti-phishing, anti-spam and anti-malware options in Microsoft Defender. It costs a few dollars per license per month and is worth the expense.
- Invest in monthly cybersecurity employee awareness training. Even with the best hardware and software protections, you can’t catch every phishing email or malicious link. The Aberdeen Group found that employee security awareness training can reduce risk between 45 – 70%. Today’s best practice is to provide on-demand employee cybersecurity training through a learning portal that includes phishing training tests. These programs can be managed for you to improve results and reduce the management burden on your team.
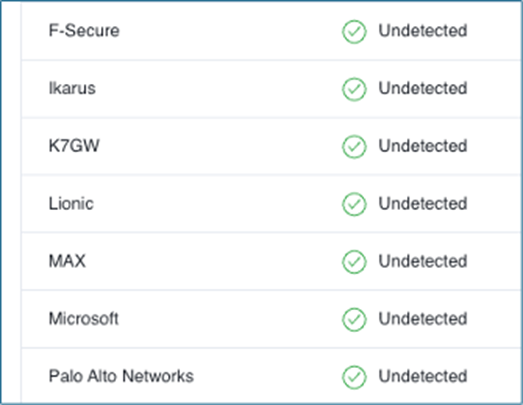
- Install Endpoint Detection and Response (EDR) or Extended Detection and Response technology (XDR). EDR and XDR are the new antivirus. Every organization should use one of these technologies to thwart attacks. When Evil Tom attacked HackMe, it was using multiple antivirus programs. As shown in the screenshot below from VirusTotal, only 8 out of 72 antivirus products flagged the executable program in the phishing attack as malicious. So, 88% of antivirus programs, including Microsoft, Symantec, Sentinel One, and other big names, missed the malware that Evil Tom wrote in 30 minutes. EDR and XDR offer much stronger protection.

2) Internal Reconnaissance. Once inside, Evil Tom leverages Erik L. User’s access to search for file shares and web servers on the local network by using a port scanning tool. One of the servers that pops up on his radar is the administrative web interface of a printer, in addition to multiple file servers. This gives Evil Tom information that he will use to expand his access.
How can you prevent this from happening?
- Network Segmentation. Regardless of how hackers get into your computer, network segmentation is a basic yet very effective way to limit the amount of your network a hacker can access if they enter your environment. Read 7 Network Segmentation Best Practices That Stop Malware’s Lateral Spread for more information.
- Use network detection and response tools. NDR tools like Extrahop, port scan detection tools like PortSentry, and IDS tools such as Zeke, Snort, or Suricata can detect and alert you when an attacker is scanning your network. But you also have to actively monitor these tools, otherwise you will miss the alerts. If you have limited staff, consider EDR/XDR solutions that can automatically block the hacker’s access when they detect these scanning activities.
3) Printer Hacking! Printers are frequently a steppingstone for hackers and overlooked by defenders. In this case, Evil Tom was able to browse the printer’s web application and access many of its configuration settings without any authentication. The default setting for many printers is to allow access to its web application without a password. For printers with a password, many users forget to change the default password which is available via a quick Google search.
This smart printer can scan documents to users’ email addresses. To do this, it is configured with a domain user account that is used to query the local LDAP server and obtain information about user email addresses.
Evil Tom decides to capture the printer’s domain credentials. To do this, he sets up a fake LDAP server—we’ll call this the Evil LDAP server. Then, he reconfigures the printer so that it attempts to query the Evil LDAP server for information, instead of the real one. At the same time, Evil Tom launches a network sniffing tool, Wireshark, which listens to the traffic sent to the Evil LDAP server.
When the printer attempts to query Evil LDAP server, the printer’s password is captured by Tom’s network sniffer. Voila! Evil Tom now has the printer’s domain credentials.
Next, Evil Tom uses an LDAP program to track all the network traffic when people sign in with their username and password and send it to his server.
How can you prevent this from happening?
- Harden your system configuration to prevent hackers from gaining access
- Turn off unnecessary services or segment them properly so everyone can’t get to them
- Require strong authentication for interfaces (like printers!)
- Routinely apply software patches
- Minimize access
- Restrict access to physical ports
- Use file and device encryption
- Install and use security software
- Employ logging software and monitoring, and more….
4) The Hacker Expands Access. Evil Tom runs an automated program to determine where the printer has read/write access. He finds access to a file share containing backups. Searching the backups, he finds a configuration file buried deep within which contains a domain administrator password. Jackpot! This scenario is all too common: over the years, files containing passwords often accumulate in unexpected file shares, left by previous IT administrators or contractors that never cleaned things out.
Using the stolen administrator password, Evil Tom now has access to all of HackMe’s files including accounts, billing, financial details, and more.
How can you prevent this from happening?
- Use the principle of least privilege. Only give each employee the exact amount of access they need to do their job. Regardless of how hackers get into your computer, if you can make it difficult for an attacker to access sensitive data, you can limit the damage. You can also manage this with role-based access permissions; restricting access can stop a hacker from expanding their privileges.
- Create smart default permissions policies that provide minimal access. Increase it only as needed.
- Consider Identity and Access Management software. A tool like Azure Active Directory offers centralized control and can help detect if an account is misused, facilitate response, and includes audit capabilities to regularly check and edit user permissions.
- Routinely conduct data discovery and mapping exercises. Whether you use automated scans or manual review, identify where your sensitive information such as PII, credit card information, etc. is stored and limit access.
5) Takeover! Evil Tom uses RDP to remotely connect to the domain controller using the stolen administrator password. From there, he uses a tool to dump all credentials from the domain controller. For any encrypted passwords he uses an automated password cracking tool that makes billions of guesses in seconds to decrypt the information. Evil Tom now has full access to HackMe’s network and can login with administrative access to the entire organization and encrypt the whole network.
How can you prevent this from happening?
a. Deploy multifactor authentication. This can stop a hacker in their tracks. It’s not just for external servers; using MFA for internal administrator access could have stopped Evil Tom from connecting to HackMe’s domain controller and thwarted his takeover plans.
b. Conduct annual penetration tests. Penetration tests by ethical hackers are one of the best ways to find your weaknesses before a criminal can exploit them. You’ll get an accurate understanding of your risk and a list of issues and weaknesses that automated scans won’t detect. If HackMe had recently had a penetration test, the misconfigurations, missed patches, and cyber hygiene issues could have been caught and proactively corrected to detect the hacker and minimize the damage he caused in the network.
We hope you found this example of how hackers get into your computer and environment helpful! If you’d like to see the video of Evil Tom’s attack on HackMe, Inc., watch our 11-minute video of how hackers get into your computer or the full 1-hour on-demand webinar. Now that you know how a hacker can access your environment and some steps to prevent that access, we hope you will implement these cybersecurity tools and policies. Contact the LMG Security team if you need help.
This blog is distributed with the permission of LMG Security.
ABOUT LMG SECURITY
LMG Security is a full-service cybersecurity firm, providing one stop shopping for a wide array of cybersecurity services. Whether you need virtual CISO or regulatory compliance consulting services, testing, solution integration, training or one of our many other services – our expert team has you covered. Our team of recognized cybersecurity experts have been covered on the Today Show and NBC News, as well as quoted in the New York Times, Wall Street Journal, and many other publications. In addition to online cybersecurity training, LMG Security provides world-class cybersecurity services to a diverse client base located around the United States and internationally.
